Configuring IPv4 Network Settings¶
| Setting | Default | AWI | OSD | Management Console |
|---|---|---|---|---|
| Enable DHCPv4 | Enabled | |||
| IP Address | ||||
| Subnet Mask | ||||
| Gateway | ||||
| Primary DNS Server | ||||
| Secondary DNS Server | ||||
| Domain Name | ||||
| FQDN | ||||
| Ethernet Mode | Auto | |||
| Maximum MTU Size | 1200 bytes | |||
| Enable 802.1X security | ||||
| Identity | ||||
| Authentication | TLS | |||
| Client Certificate | ||||
| Enable 802.1X Support for Legacy Switches |
From the OSD and AWI Network pages, you can manually configure network settings if DHCP is disabled, as well as configure 802.1x security to ensure that only authorized devices access the network.
The Static Fallback Network Configuration
The PCoIP Zero Client has a default static fallback configuration that is applied if enabled and a DHCP server is not found on the network. The specific configuration can be different for different brand names of PCoIP Zero Clients. This configuration can be disabled or enabled, and configured through the Management Console. The configurable settings are found in the NETWORK category of a profile when IPv4 is enabled and DHCPv4 is disabled. The configurable settings are:
- Static Fallback IPv4 Address: The IPv4 address applied to the zero client when a DHCPv4 server is not reached.
- Static Fallback IPv4 Subnet Mask: The IPv4 subnet mask applied to the zero client when a DHCPv4 server is not reached.
- Static Fallback IPv4 Gateway: The IPv4 gateway address applied to the zero client when a DHCPv4 server is not reached.
- Static Fallback IPv4 Timeout: The time it takes before the static fallback configuration is applied.
From the OSD and AWI, you can also configure IPv6 network settings. To configure IPv6 settings, see Configuring IPv6 Network Settings.
You can also configure a subset of network settings from the AWI Initial Setup page.
You can also configure network settings (DHCP, IP address, subnet mask, gateway, and primary and secondary DNS servers) from the AWI Initial Setup page. To configure network settings from this page, see Configuring Initial Setup Parameters.
Setting up 802.1x authentication
For a description of all the components you need to configure 802.1x authentication, as well as the detailed steps you need to follow to configure the authentication, see Configuring 802.1x Network Device Authentication.
You configure network settings from the OSD and AWI Network pages (shown next).
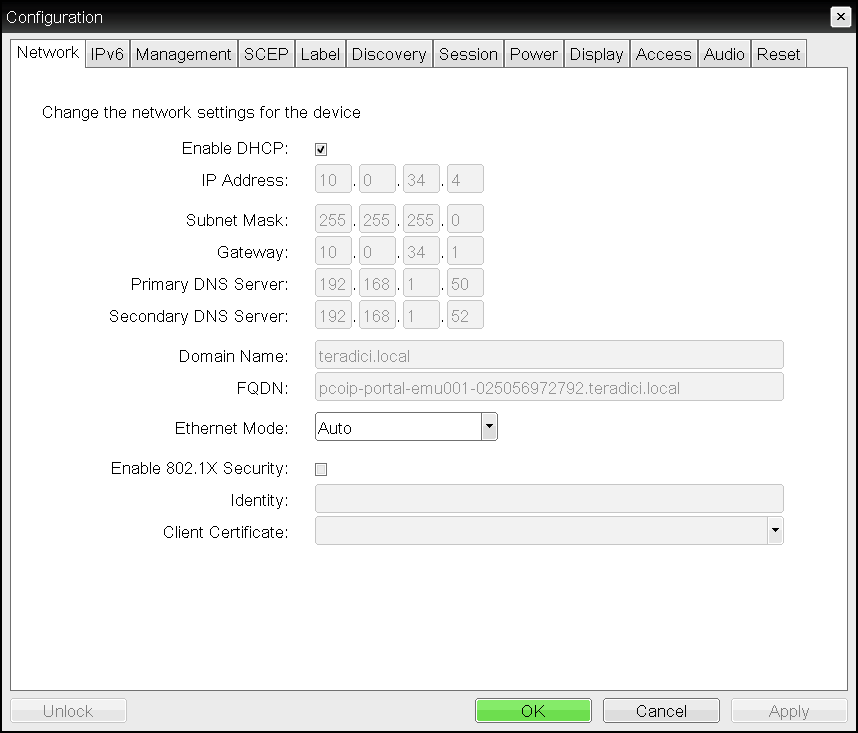
OSD Network page
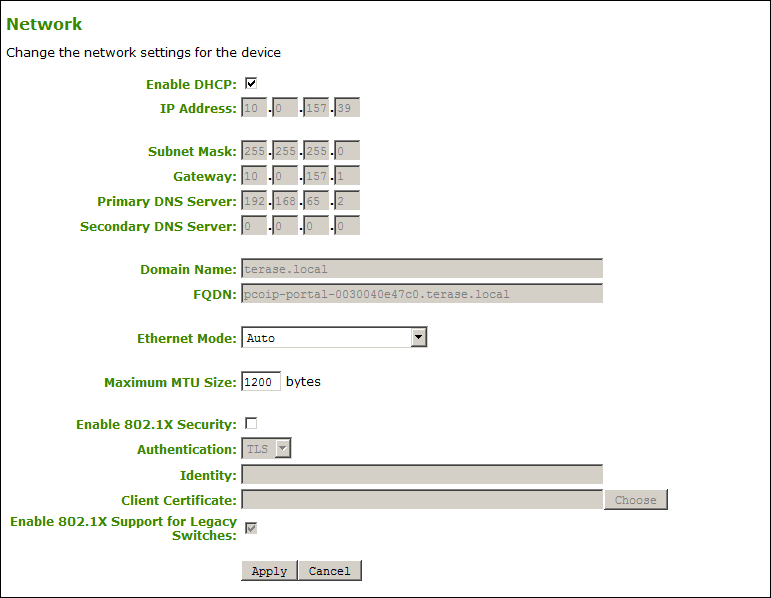
AWI Network page
The following parameters display on the OSD and AWI Network pages:
Network Parameters
| Parameter | Description |
|---|---|
| Enable DHCP | When enabled, the device contacts a DHCP server to be assigned an IP address, subnet mask, gateway IP address, and DNS servers, and also requests a domain name (option 15), host name (option 12), and client Fully Qualified Domain Name (FQDN). When disabled, you must set these parameters manually. |
| IP Address | The device’s IP address. If DHCP is disabled, you must set this field to a valid IP address. If DHCP is enabled, you cannot edit this field. |
| Subnet Mask | The device’s subnet mask. If DHCP is disabled, you must set this field to a valid subnet mask. If DHCP is enabled, you cannot edit this field. Warning: Take care when setting the subnet mask It is possible to configure an invalid IP address/subnet mask combination (for example, invalid mask) that leaves the device unreachable. Take care when setting the subnet mask. |
| Gateway | The device’s gateway IP address. If DHCP is disabled, this field is required. If DHCP is enabled, you cannot edit this field. |
| Primary DNS Server | The device’s primary DNS IP address. This field is optional. If the DNS server IP address is configured when using a connection manager, the connection manager address may be set as an FQDN instead of an IP address. |
| Secondary DNS Server | The device’s secondary DNS IP address. This field is optional. If the DNS server IP address is configured when using a connection manager, the connection manager address may be set as an FQDN instead of an IP address. |
| Domain Name | The domain name of the device (for example, domain.local). This field is optional. |
| FQDN | The fully qualified domain name for the device. The default is pcoip-portal- To use the FQDN feature, the DNS server with DHCP option 81 must be available and properly configured. |
| Ethernet Mode | Lets you configure the Ethernet mode of the client as follows:
Warning: Different parameters may result in a loss of network connectivity When Auto-Negotiation is disabled on the PCoIP device, it must also be disabled on the switch. Additionally, the PCoIP device and switch must be configured to use the same speed and duplex parameters. Different parameters may result in a loss of network connectivity. Click OK to change the parameter. Note: Use 10 Mbps Full-Duplex and 100 Mbps Full-Duplex with caution You should always set the Ethernet mode to Auto and only use 10 Mbps Full-Duplex or 100 Mbps Full-Duplex when the other network equipment (for example, a switch) is also configured to operate at 10 Mbps full-duplex or 100 Mbps full-duplex. An improperly set Ethernet mode may result in the network operating at half-duplex, which is not supported by the PCoIP protocol. The session will be severely degraded and eventually dropped. |
| Maximum MTU Size (AWI only) |
Lets you configure the Maximum Transfer Unit packet size. A smaller MTU may be needed for situations such as VPN tunneling because PCoIP packets cannot be fragmented. Set the Maximum MTU Size to a value smaller than the network path MTU for the end-to-end connection between the host and client. The Maximum MTU Size range is 600 to 1500 bytes for all firmware versions. The default MTU size is 1200. |
| Enable 802.1X Security | Enable this field for each of your PCoIP Remote Workstation Cards and Tera2 PCoIP Zero Clients if your network uses 802.1x security to ensure that only authorized devices access the network. If enabled, configure the Authentication, Identity, and Client Certificate fields. |
| Authentication (AWI only) |
This field is set to TLS (Transport Layer Security) and is grayed-out. TLS is currently the only authentication protocol supported. |
| Identity | Enter the identity string used to identify your device to the network. Should be the Common Name (CN ) or subject name (SN ) of the 802.1x certificate entered in the Client Certificate field. |
| Client Certificate | Click Choose to select the client certificate you want to use for your 802.1x devices. The list of certificates that appears includes the certificates uploaded from the Certificate Upload page that contain a private key. The certificate you choose from the Network page is linked to the read-only Client Certificate field on the Certificate Upload page. Note: 802.1x client certificate must contain all security details PCoIP only supports one 802.1x client certificate. Ensure your security details are all contained within the one file. The 802.1x certificate must contain a private key. |
| Enable 802.1X Support for Legacy Switches (AWI only) | When enabled, enables greater 802.1x compatibility for older switches on the network. |
To configure network settings:
-
Open the Network page:
- From the OSD, select Options > Configuration > Network.
- From the AWI, select Configuration > Network.
-
From the OSD or AWI Network page, configure the network settings.
-
To save your updates, click OK from the OSD, or click Apply from the AWI.