Creating and Applying Custom Certificates¶
In order to securely connect your PCoIP Zero Client to a Remote Workstation Card, the certificates must meet PCoIP Zero Client and PCoIP Remote Workstation Card Suite B requirements and both devices must be configured correctly.
This reference provides the Suite B certificate requirements so that you can create your own custom certificate to securely connect your PCoIP Zero Client to a Remote Workstation Card. It also provides the configuration steps to connect your endpoints using the Suite B: TLS 1.2 with Suite B-compliant 192-bit elliptic curve encryption TLS Security Mode parameter.
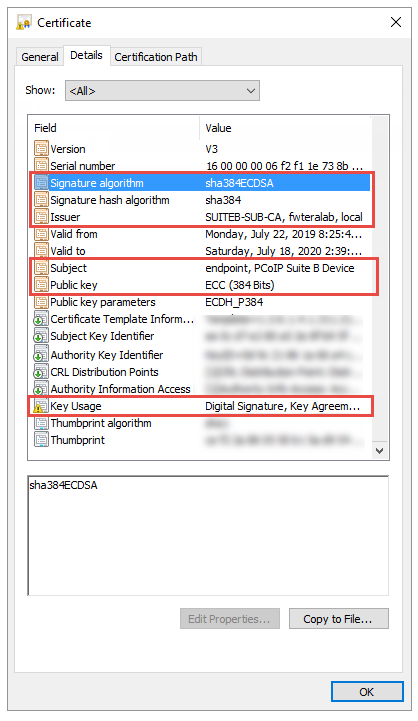
Required Certificate Parameters
All Certificate Requirements (Root/Client/Server)¶
-
Subject and Issuer name must be valid (both the CN and O and cannot be empty).
-
Signature algorithm must be SHA-384ECDSA.
-
Signature hash algorithm must be SHA-384.
-
Public key needs to be an 384 bit elliptic curve key that was generated from the secp384r1 curve (commonly known as the P-384 curve).
-
Must be generated as unencrypted .pem files.
Client Certificate Specific Requirements¶
-
Key Usage must be Digital Signature or omitted.
-
Self signed certificates are not allowed.
Server Certificate Specific Requirements¶
- Key Usage must be Key Agreement, Key Encipherment or omitted.
- Self signed certificates are not allowed.
Notes
-
The validity period is optional.
-
The Certificate Revocation List (CRL) lookup and Online Certificate Status Protocol (OCSP) is not used.
-
If certificate key usage has both Digital Signature and Key Agreement (or if certificate has no Key Usage), then it is possible to use the same certificate on both host and client.
-
See samples for Zero Client (client), Remote Workstation Card (server), and Root CA certificates.
-
The Generate_Certificate_Script package has been provided to demonstrate how to generate custom certificates. Unzip and run the example_suiteb_all_gen.sh script (certificates will be created in the certificates folder).
Perform the following configuration steps on the Remote Workstation Card and Zero Client to establish a secure connection with your custom certificates.
Remote Workstation Card Configuration¶
-
Login to the Remote Workstation Card AWI.
-
Browse to Upload > Certificate and Upload both the issuer (example_suite_b_root_ca_cert.pem) and client (example_suite_b_server.pem) certificates.
-
Browse to Configuration > Session.
-
Select Direct from Client for session connection type and select Show Advanced Options.
-
Select Suite B: TLS 1.2 with Suite B-compliant 192-bit elliptic curve encryption for TLS Security Mode parameter.
-
Select the correct Server certificate for the Peer-to-Peer Certificate parameter.
Zero Client Configuration¶
-
Login to the Zero Client AWI.
-
Browse to Upload > Certificate and Upload both the issuer (example_suite_b_root_ca_cert.pem) and client (example_suite_b_client.pem) certificates.
-
Browse to Configuration > Session.
-
Select Direct to Host for the Session Connection Type and enter the IP address of the Remote Workstation Card that you are connecting to for the DNS Name or IP Address parameter.
-
Select Show Advanced Options and select Suite B: TLS 1.2 with Suite B-compliant 192-bit elliptic curve encryption for the TLS Security Mode parameter.
-
Select the correct Client certificate for the Peer-to-Peer Certificate parameter.
-
From the OSD connect to your Remote Workstation Card.
Note
If a custom peer to peer certificate is applied and a connection is made, and the custom certificates is removed from the certificate store on either device, a subsequent connection will not establish.