Anyware Connector Multi-Factor Authentication
Duo Authentication¶
If you wish to use Duo authentication with Anyware Connector you will be required to setup an authentication server provided by Duo. For more information on this, see Duo Authentication Proxy - Reference.
Duo Authentication Version
The Connector was tested with Duo version 2.4.21.
The following are key items in the authproxy.cfg file that are relevant for the Anyware Connector configuration:
[duo_only_client]
[radius_server_duo_only]
ikey=<integration key for duo>
skey=<secret key for duo>
api_host=<host used for duo>
radius_ip_1=<cac connection server ip>
radius_secret_1=<shared secret for above>
radius_ip_2=<cac connection server ip2>
radius_secret_2=<shared secret for above>
port=1812
Azure MFA Authentication¶
Microsoft Azure MFA Component Versions
We tested the Connector with Microsoft Azure MFA on November 15th 2019 with the following components.
HP component versions:
- PCoIP Software Client for Windows 19.11.
- Connector with MFA flag enabled.
- PCoIP Standard/Graphics Agent 19.11.
3rd party component versions:
- Azure Active Directory Premium or Microsoft 365 Business offering to use Azure MFA.
- Network Policy Server (NPS) acting as the RADIUS server.
- NPS extension 1.0.1.32.
- Microsoft Authenticator App 1911.7724 (Android/iOS).
Using different versions may result in different behavior and has not been tested by us.
Azure MFA Configuration¶
If you wish to use Azure MFA with the Connector you need to configure a number of 3rd party components. The following steps outline this process:
- From within the Azure portal click Azure AD.
- Click Enable MFA for target users.
- Install the Microsoft Authenticator App on an Android or iOS mobile device.
- Ensure that if the users requiring MFA are not yet populated in Azure AD, that you setup Azure AD Connect to sync On-Premises users to Azure.
- Install Network Policy and Access role on Windows Server 2016 or 2019.
- Install Network Policy Server (NPS) extension for Azure MFA.
- Register NPS to Active Directory to enable it to query the list of users.
Once you have registered the NPS you need to configure the server. The following steps outline the NPS configuration:
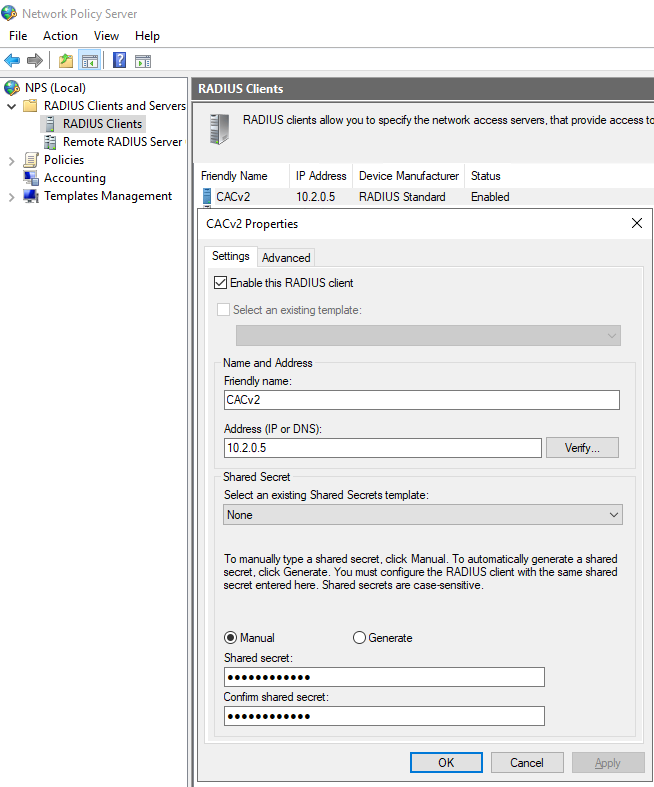
- From within the NPS console click RADIUS Clients.
- Add the Connector IP address and Shared Secret and click OK.
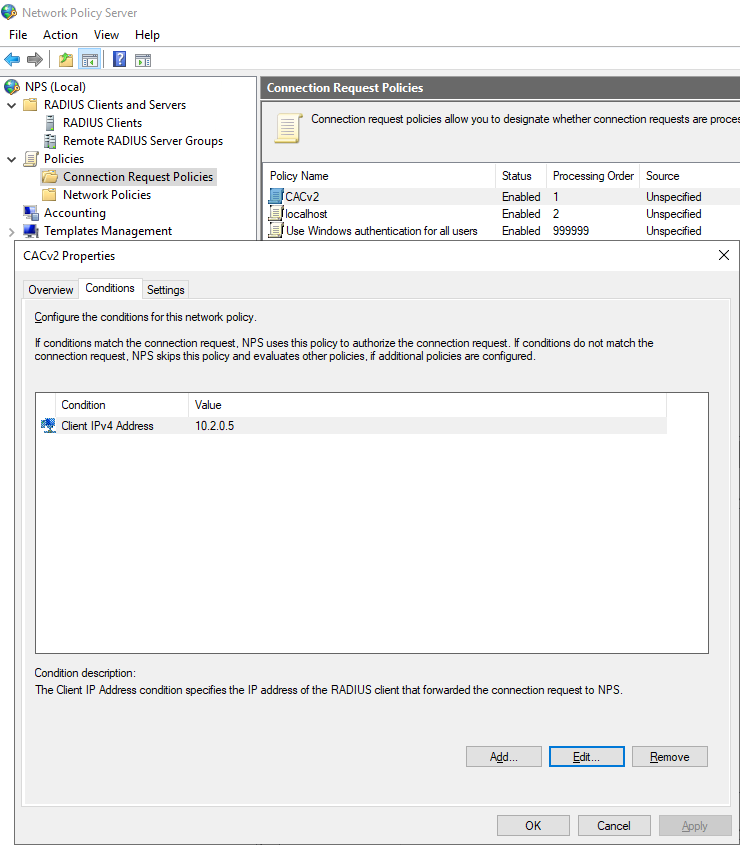
- Click Policies > Connection Request Policies and add a new policy name and click OK.
- From the Conditions tab add the Client IPv4 Address of the Connector and click OK.
- From the Settings tab under Authentication click Accept users without validating credentials.
- Restart NPS services to enable these changes to take effect.