Enable Federated Authentication for Anyware Manager with SSO
To use the Federated Authentication feature seamlessly you must have the lastest versions of all the HP Anyware software component such as the Software Client, Software Agent, and the Anyware Manager installable. This is not applicable if you are using Anyware Manager as a Service. When Federated Authentication is configured, you should enable it from the Admin Console.
To Enable Federated Authentication:¶
There are two methods of configuring Federated User Authentication in Anyware Manager, through the Admin Console, or the Connector installer.
1. Admin Console configuration¶
Global Configuration¶
Federated Authentication can be configured for your entire deployment using the Global configuration method. The steps are:
- Navigate to https://cas.teradici.com and open the web console.
- Enable the Beta toggle to turn on Beta mode, near the top of the interface. Select Yes, I am in! in the dialog box.
- Select your deployment from the drop down, click the kebab (3 vertically stacked circles) next to your deployment's name and select Edit deployment.
- Open the Deployment Settings section and select Connector Settings.
-
Enable OAuth Authentication and enter in authentication URL and client ID. To obtain the OAuth client ID, you need to login into Okta IDP and navigate to the Applications tab from the left pane. Please refer the highlighted area in the image below:
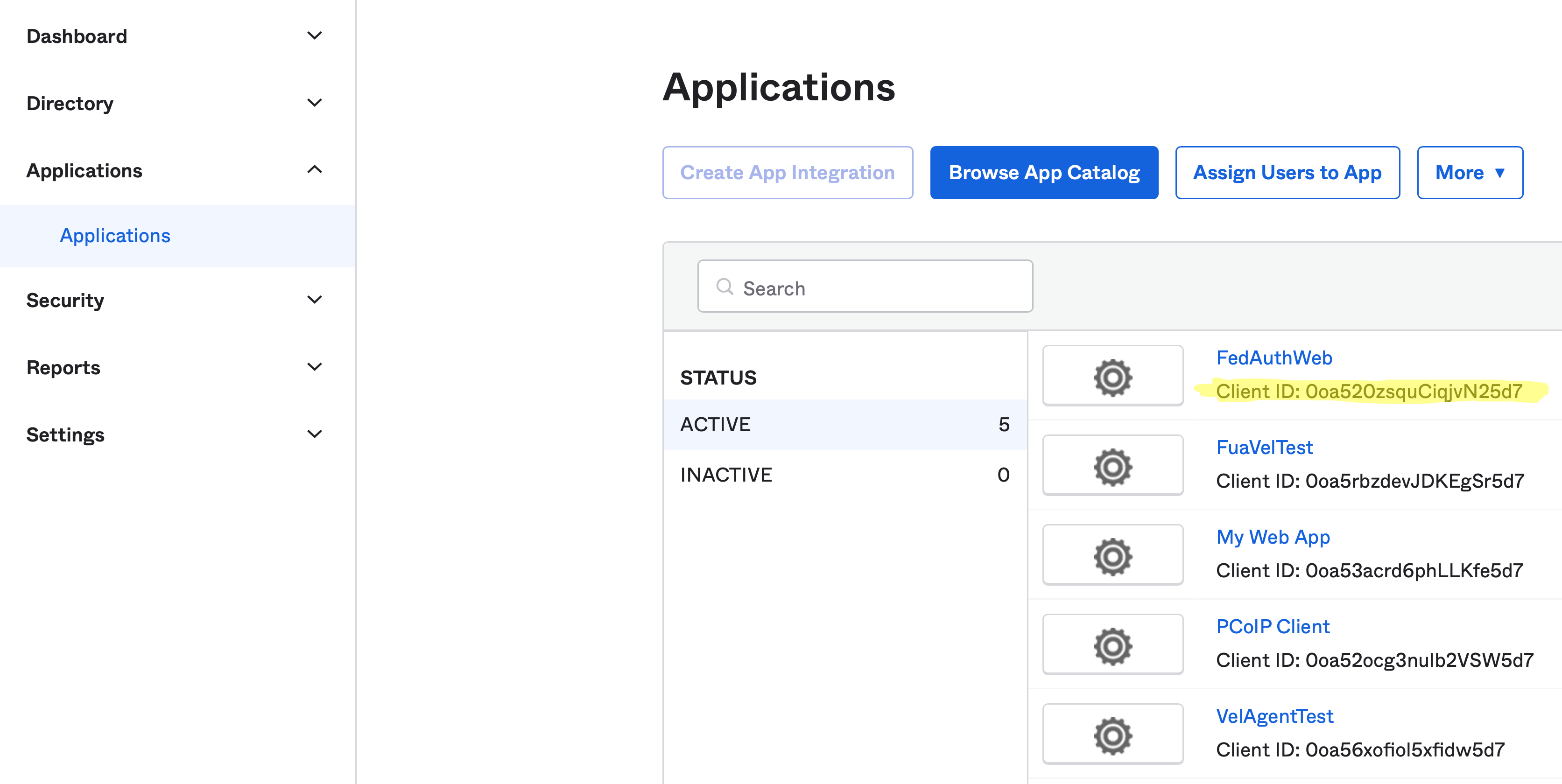
-
Click Save Configuration.
Federated Authentication is now configured.
Per Connector Configuration¶
Federated User Authentication can be configured on a per connector basis. This permits you to try it out on a single connector to start to minimize impact to your deployment or to have specific connectors that are used for Federated User Authentication:
- Select your deployment from the Deployment drop down option.
- Click Connectors from the left pane and select the connector you wish to modify from the table.
- Select the Connector Settings tab and click Enabled under OAuth Authentication.
- Enter the following information into the interface that you obtained from your Identity Provider configuration:
- Authorization URL
- Client ID
- Click Save Configuration.
Federated Authentication is now configured.
After configured the setting in admin console, run the following command in connector to apply the setting:
Private Key and CA requirement
Ensure that you have the PEM files for the signed certificate, private key and certificate revocation list from the above instructions on Preparing for Single Sign-On, and have uploaded them via sftp to each Connector.
- To enroll by the private key and certificate of the Certification Authority (available in 23.01 and later):
- To update a Connector to use this setting:
- Log into the Connector using SSH.
- Run the command:
sudo cloud-access-connector update <any other configuration flags you use> --pull-connector-config --sso-signing-csr-ca <path to pem> --sso-signing-csr-key <path to pem> --sso-signing-crl <path to crl> --sso-enrollment-url "" --sso-enrollment-domain "" --sso-enrollment-username "" --sso-enrollment-password "" --sso-enrollment-certificate-template-name "".
- Run the command:
- Log into the Connector using SSH.
- To deploy a new Connector to use this setting:
- Log into the Connector using SSH.
- Run the command:
sudo cloud-access-connector install <any other configuration flags you use> --pull-connector-config --sso-signing-csr-ca <path to pem> --sso-signing-csr-key <path to pem> --sso-signing-crl <path to crl>.
- To update a Connector to use this setting:
- To enroll via Active Directory Certification Authority Web Enrollment (available in 23.01 and later):
- To update a Connector to use this setting:
- Log into the Connector using SSH.
- Run the command:
sudo cloud-access-connector update <any other configuration flags you use> --pull-connector-config --sso-enrollment-url "$Enrollment_URL" --sso-enrollment-domain "$Domain" --sso-enrollment-username "$User_Name" --sso-enrollment-password "$Password" --sso-enrollment-certificate-template-name "$Template_Name"--sso-signing-csr-ca "" --sso-signing-csr-key "" --sso-signing-crl "".
- To deploy a new Connector to use this setting:
- Log into the Connector to using SSH.
- Run the command:
sudo cloud-access-connector install <any other configuration flags you use> --pull-connector-config --sso-enrollment-url "$Enrollment_URL" --sso-enrollment-domain "$Domain" --sso-enrollment-username "$User_Name" --sso-enrollment-password "$Password" --sso-enrollment-certificate-template-name "$Template_Name".
- To update a Connector to use this setting:
2. OAuth Configuration for Connectors¶
You can configure your environment at the connector using the command line interface (CLI) on each connector in your environment.
To enroll by the private key and certificate of the Certification Authority:¶
Private Key and CA requirement
Ensure that you have the PEM files for the signed certificate, private key and certificate revocation list from the above instructions on Preparing for Single Sign-On, and have uploaded them via sftp to each Connector.
Passphrase Protection
Passphrase protection for CA certificates is not supported.
If you are installing a new connector:
- Run this command:
sudo cloud-access-connector install […other settings...] --enable-oauth true --id-provider-url https://id.provider.com --oauth-client-id XXXXXXXXX --enable-sso true --sso-signing-csr-ca <path to pem> --sso-signing-csr-key <path to pem> --sso-signing-crl <path to crl>.
If you are configuring an existing connector:
- Run this command (for 23.01 or later):
sudo cloud-access-connector update […other settings...] --enable-oauth true --id-provider-url https://id.provider.com --oauth-client-id XXXXXXXXX --enable-sso true --sso-signing-csr-ca <path to pem> --sso-signing-csr-key <path to pem> --sso-signing-crl <path to crl> --sso-enrollment-url "" --sso-enrollment-domain "" --sso-enrollment-username "" --sso-enrollment-password "" --sso-enrollment-certificate-template-name "".
To enroll via Active Directory Certification Authority Web Enrollment (available in 23.01 and later):¶
If you are installing a new connector:
- Run this command:
sudo cloud-access-connector install […other settings...] --enable-oauth true --id-provider-url https://id.provider.com --oauth-client-id XXXXXXXXX --enable-sso true --sso-enrollment-url "$Enrollment_URL" --sso-enrollment-domain "$Domain" --sso-enrollment-username "$User_Name" --sso-enrollment-password "$Password" --sso-enrollment-certificate-template-name "$Template_Name".
If you are configuring an existing connector:
- Run this command:
sudo cloud-access-connector update […other settings...] --enable-oauth true --id-provider-url https://id.provider.com --oauth-client-id XXXXXXXXX --enable-sso true --sso-enrollment-url "$Enrollment_URL" --sso-enrollment-domain "$Domain" --sso-enrollment-username "$User_Name" --sso-enrollment-password "$Password" --sso-enrollment-certificate-template-name "$Template_Name" --sso-signing-csr-ca "" --sso-signing-csr-key "" --sso-signing-crl "".
Installation Flags¶
| Flag | Type | Description |
|---|---|---|
--enable-oauth |
Boolean | Enables Oauth authentication. (Default=False) |
--id-provider-url |
String | Sets the identity provider URL. Example: --id-provider-url https://provider-1234567890.okta.com. This flag is required if --enable-oauth is true. |
--oauth-client-id |
String | Gets the Client ID from the Identity Provider. This flag is required if --enable-oauth is true. |
--fa-url |
String | The Federated Auth Broker URL. for example https://cac-vm-fqdn:port |
--oauth-flow-code |
String | Specify the oauth flow / grant type (default "OAUTH_FLOW_CODE_WITH_PKCE"). "OAUTH_FLOW_CODE_WITH_PKCE" is the only supported oauth flow for now |
--enable-entitlements-by-upn |
Boolean | Enables/Disables searching entitlements by UPN. This flag is required to be true, if --enable-oauth is true. |
--sso-signing-csr-ca |
String | Path to copy intermediate CA Certificate. |
--sso-signing-csr-key |
String | Path to the intermediate key. |
--sso-signing-crl |
String | Path to a certificate revocation list. |
--sso-enrollment-url |
String | Gets the URL to the Active Directory Certification Authority Web Enrollment Service. |
--sso-enrollment-domain |
String | Domain of the user to access Active Directory Certification Authority Web Enrollment Service. |
--sso-enrollment-username |
String | Username for accessing Active Directory Certification Authority Web Enrollment Service. |
--sso-enrollment-password |
String | Password for the username to access Active Directory Certification Authority Web Enrollment Service. |
--sso-enrollment-certificate-template-name |
String | Name of the certificate template that Active Directory Certificate Services (AD CS) uses to sig CSR. |
After Completion of Testing¶
After you have completed trying the feature our, or testing it. We recommend you revoke the Intermediate Signed Certificate and Private Key you generated to enable SSO.
If you had configured this in production Connectors you need to turn off SSO. This can be done using the instructions above from the Admin Console and switching Enable Single Sign-On (SSO) so that it is disabled, or from the command line for each connector using:
- Run the command:
sudo cloud-access-connector update […other settings...] --enable-sso false.