Uploading Certificates¶
You can upload and manage your CA root and endpoint certificates from the AWI's Certificate Upload page, shown below.
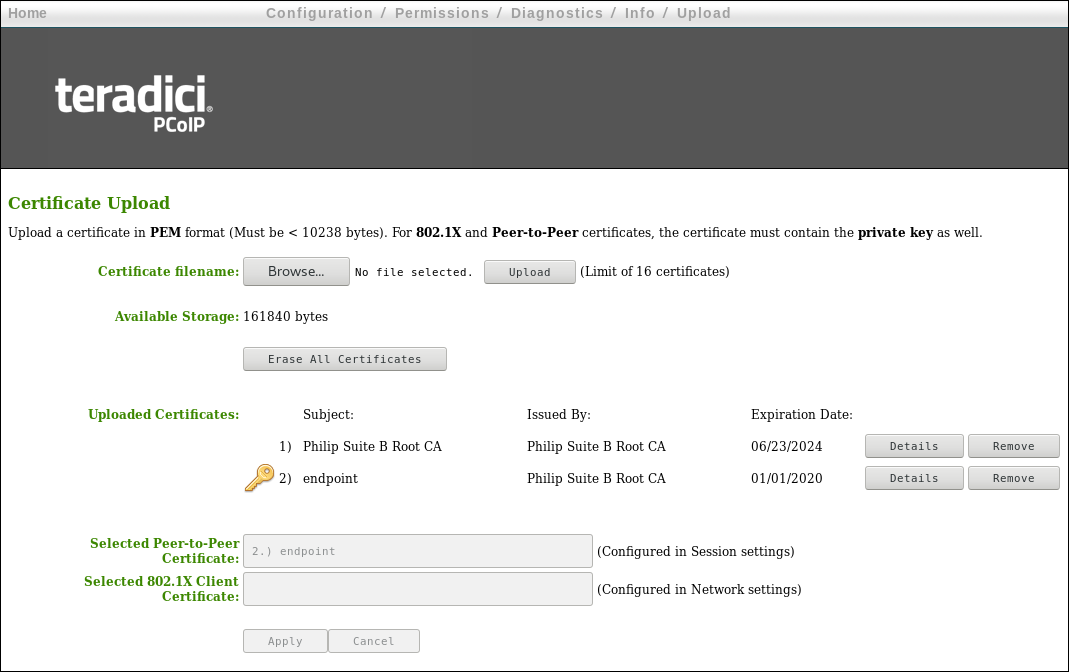
AWI Certificate Upload Page
You can simplify the retrieval and installation of digital certificates by enabling devices to obtain certificates automatically from a Simple Certificate Enrollment Protocol (SCEP) server. To upload certificates automatically using SCEP, see Obtaining Certificates Automatically Using SCEP.
Certificates used in PCoIP firmware must be in PEM format with a maximum file size of 10,237 bytes, and maximum RSA key size of 4096 bits. You can upload up to 16 certificates providing you don't exceed the maximum storage size of 163,648 bytes. Each SCEP usage type takes up one of the total number of certificates for upload. As an example, if there are 4 different usage types for certificates obtained using SCEP, there will be room for 12 remaining certificate uploads. The Available Storage field lets you know how much space is left in the certificate store. The Details button allows you to view information about the particular certificate such as SCEP usage and key type.
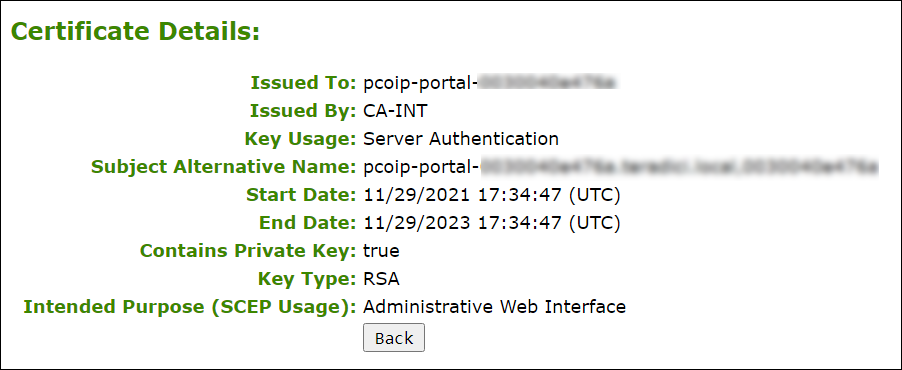
Certificate Details Information
Authentication issues
If you have authentication issues after uploading a Connection Server client certificate, see PCoIP TROUBLESHOOTING STEPS: View Connection Server Client Certificates (KB 1363) for further information.
Include all security information in 802.1X client certificate
The PCoIP protocol reads just one 802.1X client certificate for 802.1X compliant networks. Make sure you include all the security information for your PCoIP devices in that client certificate. For more information about uploading certificates, see Certificate management for PCoIP Zero Clients and Remote Workstation Cards (KB 1561). For information on 802.1X certificate authentication, see Configuring 802.1X Network Device Authentication.
Syslog TCP/TLS Authentication¶
The Syslog TCP with TLS connection type should be used when you want to establish a secure connection between your endpoints and the Syslog Server. Consider the following requirements when you use the Syslog TCP with TLS connection type to connect to your Syslog server.
-
Syslog TCP/TLS authentication requires at a minimum one certificate (a Syslog server CA root certificate)and if Mutual Authentication is required, a secondary certificate (a Syslog client certificate).
-
The Syslog client certificate must be in .pem format and contain a private key that uses RSA encryption. If the certificate is in a different format, you must first convert the certificate, including the private key, to .pem format before uploading it.
-
After uploading the Syslog client certificate from the AWI Certificate Upload page, you must configure Syslog authentication from the AWI Event Log page. This entails changing the Syslog Connection Type to TCP with TLS, selecting the correct Syslog client certificate from the drop-down list, and applying your settings.
-
The Syslog server CA root certificate must be in .pem format, but should not need to contain a private key. If the certificate is in a different format, you must convert it to .pem format before uploading it. This certificate does not require configuration from the Event Log page.
-
Both the Syslog client certificate and the Syslog server CA root certificate must be less than 10,238 bytes; otherwise, you will not be able to upload them. Some certificate files may contain multiple certificates. If your certificate file is too large and it has multiple certificates within, you can open the file in a text editor, copy and save each certificate to its own file.
802.1X Authentication¶
Consider the following requirements when you use 802.1X authentication.
-
802.1X authentication requires two certificates—an 802.1X client certificate and an 802.1X server CA root certificate.
-
The 802.1X client certificate must be in .pem format and contain a private key that uses RSA encryption. If the certificate is in a different format, you must first convert the certificate, including the private key, to .pem format before uploading it.
-
After uploading the 802.1X client certificate from the Certificate Upload page, you must configure 802.1X authentication from the Network page. This entails enabling 802.1X authentication, entering an identity string for the device, selecting the correct 802.1X client certificate from the drop-down list, and applying your settings.
-
The 802.1X server CA root certificate must be in .pem format, but should not need to contain a private key. If the certificate is in a different format, you must convert it to .pem format before uploading it. This certificate does not require configuration from the Network page.
-
Both the 802.1X client certificate and the 802.1X server CA root certificate must be less than 10,238 bytes; otherwise, you will not be able to upload them. Some certificate files may contain multiple certificates. If your certificate file is too large and it has multiple certificates within, you can open the file in a text editor, copy and save each certificate to its own file.
The following settings display on the AWI Certificate Upload page.
Certificate Upload Page Parameters
| Parameter | Description |
|---|---|
| Certificate filename | Used to select a certificate to upload. Upload up to a maximum of 16 root and client certificates. |
| Available Storage | Amount of remaining storage space to add additional certificates. |
| Uploaded Certificates | This displays any uploaded certificates. |
| Selected Peer-to-Peer Certificate | This is a read-only field. It is linked to the Peer-to-Peer Certificate field on the Session page. |
| 802.1X Client Certificate | This is a read-only field. It is linked to the Client Certificate field on the Network page. |
To upload a certificate to a client:
-
From the AWI, select the Upload > Certificate.
-
Browse to the folder containing the certificate file. This file will have a
.pemextension. -
Double-click the correct
.pemcertificate file. -
Click Upload.
-
Click OK to confirm that you want to proceed with the upload.
-
Click Continue.
If the certificate uploads successfully, it will appear in the Uploaded Certificates section on this page.