Configuring firewalld for New Installs of Management Console 20.04 or newer¶
As of release 20.04, Management Console was upgraded for use with firewalld. Current versions of Management Console do not configure any firewall settings, but instead leaves firewall configurations in control of the administrator. In earlier versions of Management Console, the installer would enable iptables, create and apply a new set of rules that would allow the Management Console to communicate properly. Therefore, firewall configurations were not required for releases 20.01 or older.
If you you are using a firewall with Management Console on your Linux system, you must follow the recommended instructions that show how to create the rules required for Management Console communications. You must also add additional rules required to meet the requirements of your corporate security policy.
The steps below are instructions for configuring firewalld, grouped by IPv4 and IPv6 environments.
To configure firewalld in IPv4 environment
RPM New Installations: To configure firewalld in IPv6 environment
OVA New Installations: To configure firewalld in IPv6 environment
Firewalld default behaviours when enabled
-
All inbound connections are tested against configured rules that have been applied
-
All outbound connections are allowed
-
Rules to allow traffic are added to the default zone. All other traffic will be blocked.
Uninstalling RPM
Uninstalling the Management Console RPM does not completely remove the firewall rules.
New Installs in IPv4 Environment¶
To configure firewalld for Management Console communication in an IPv4 environment perform the following steps:¶
-
Login to the Management Console host operating system console.
-
Enable firewalld.
sudo systemctl enable firewalld --now -
Get the default zone. If the default zone is trusted it will allow all packets. It is recommended that the default zone is set to public.
sudo firewall-cmd --get-defaultIf default zone is not public, execute the following commands to set the default zone to public.
sudo firewall-cmd --permanent --zone=trusted --remove-service=pcoip-agent sudo firewall-cmd --set-default=public sudo firewall-cmd --reload -
Get the default zone and assign it to a variable.
def_zone=$(firewall-cmd --get-default) -
Set the log (all denied packets logged together).
sudo firewall-cmd --set-log-denied=all -
Add an interface.
sudo firewall-cmd --zone=$(echo $def_zone) --change-interface=$(ip addr show | grep "state UP" | head -1 | awk -F': ' '{print $2}') -
Enable required ports.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-port={80,443,22,5172}/tcp -
Allow pings.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --remove-icmp-block={echo-reply,echo-request} 2>/dev/null -
Redirect port 443 to 8443.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-forward-port=port=443:proto=tcp:toport=8443 -
Enable IP Masquerading.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-masquerade -
Redirect Port 80 to 8080.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-forward-port=port=80:proto=tcp:toport=8080 -
Drop incoming packets to 127/8 from other interfaces other than loopback interface.
sudo firewall-cmd --permanent --new-zone loopback 2>/dev/null sudo firewall-cmd --permanent --zone=loopback --change-interface=lo 2>/dev/null sudo firewall-cmd --zone=loopback --permanent --set-target=ACCEPT sudo firewall-cmd --zone=loopback --permanent --add-source=127.0.0.0/8 -
Reload the firewall.
sudo firewall-cmd --reload -
Confirm the rules are applied.
-
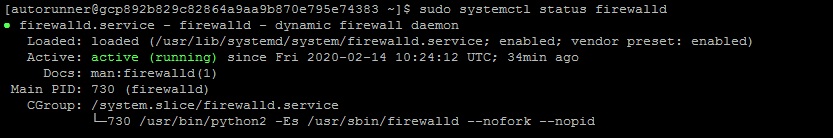
Check the firewalld status is active.
sudo systemctl status firewalld
-
Verify all rules are added in firewalld or not, all rules should be applied.
sudo firewall-cmd --list-all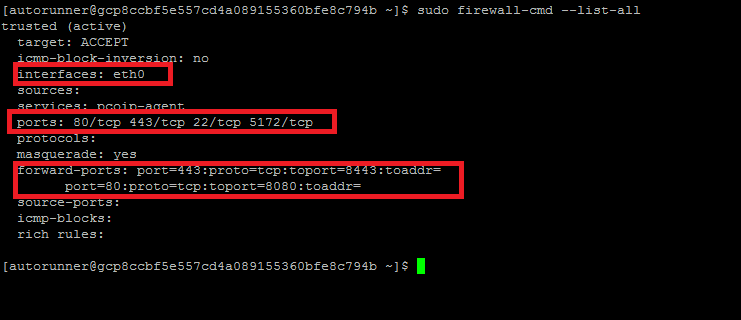
-
Firewalld Script for New Installations of Management Console 20.04 or newer Using IPv4¶
HP has provided instructions to create a script that stops the iptables service, and enables firewalld with the required IPv4 rules for Management Console to work correctly.
The script file is created and executed using the following steps:
-
Copy the script content and save into firewalld.sh
sudo vi firewalld.sh1. Provide permissions for the script to execute.#!/bin/bash val1=1 if [ $val1 -eq 1 ]; then systemctl stop iptables || service iptables stop systemctl enable firewalld --now def_zone=$(firewall-cmd --get-default) if [ $def_zone != "public" ] ; then firewall-cmd --permanent --zone=trusted --remove-service=pcoip-agent firewall-cmd --set-default=public firewall-cmd --reload def_zone=$(firewall-cmd --get-default) fi firewall-cmd --set-log-denied=all firewall-cmd --permanent --zone=$(echo $def_zone) --change-interface=`ip addr show | grep "state UP" | head -1 | awk -F': ' '{print $2}'` firewall-cmd --zone=$(echo $def_zone) --permanent --add-port={22,443,80,5172}/tcp firewall-cmd --zone=$(echo $def_zone) --permanent --remove-icmp-block={echo-reply,echo-request} firewall-cmd --zone=$(echo $def_zone) --permanent --add-forward-port=port=443:proto=tcp:toport=8443 firewall-cmd --zone=$(echo $def_zone) --permanent --add-forward-port=port=80:proto=tcp:toport=8080 firewall-cmd --permanent --new-zone loopback firewall-cmd --permanent --zone=loopback --change-interface=lo firewall-cmd --zone=loopback --permanent --set-target=ACCEPT firewall-cmd --zone=loopback --permanent --add-source=127.0.0.0/8 firewall-cmd --reload fi 2> /dev/nullsudo chmod +x ./firewalld.sh -
Run firewalld.sh:
sudo ./firewalld.sh
New Installs in IPv6 Environment¶¶
To configure firewalld for new RPM installation of Management Console allowing communication in an IPv6 environment perform the following steps:¶
-
Login to the Management Console host operating system console.
-
Enable firewalld.
sudo systemctl enable firewalld --now -
Get the default zone. If the default zone is trusted it will allow all packets. It is recommended that the default zone is set to public.
sudo firewall-cmd --get-defaultIf default zone is not public, execute the following commands to set the default zone to public.
sudo firewall-cmd --permanent --zone=trusted --remove-service=pcoip-agent sudo firewall-cmd --set-default=public sudo firewall-cmd --reload -
Get the default zone and assign it to a variable.
def_zone=$(firewall-cmd --get-default) -
Set the log (all denied packets logged together).
sudo firewall-cmd --set-log-denied=all -
Add an interface.
``` sudo firewall-cmd --permanent --zone=$(echo $def_zone) --change-interface=`ip addr show | grep "state UP" | head -1 | awk -F': ' '{print $2}'` ``` -
Enable required IPv6 ports.
-
Open port 443
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=443 protocol=tcp accept' -
Open port 22
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=22 protocol=tcp accept' -
Open port 5172
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=5172 protocol=tcp accept' -
Open port 80
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=80 protocol=tcp accept'
-
-
Allow pings.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --remove-icmp-block={echo-reply,echo-request} 2>/dev/null -
Redirect IPv6 port 443 to 8443.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 forward-port to-port=8443 protocol=tcp port=443' -
Redirect IPv6 Port 80 to 8080.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 forward-port to-port=8080 protocol=tcp port=80' -
Drop incoming packets to 127/8 from other interfaces other than loopback interface.
sudo firewall-cmd --permanent --new-zone loopback 2>/dev/null sudo firewall-cmd --permanent --zone=loopback --change-interface=lo 2>/dev/null sudo firewall-cmd --zone=loopback --permanent --set-target=ACCEPT sudo firewall-cmd --zone=loopback --permanent --add-source=127.0.0.0/8 -
Reload the firewall.
sudo firewall-cmd --reload -
Confirm the rules are applied.
-
Check the firewalld status is active.
sudo systemctl status firewalld

-
Verify all rules are added in firewalld or not, all rules should be applied.
sudo firewall-cmd --list-all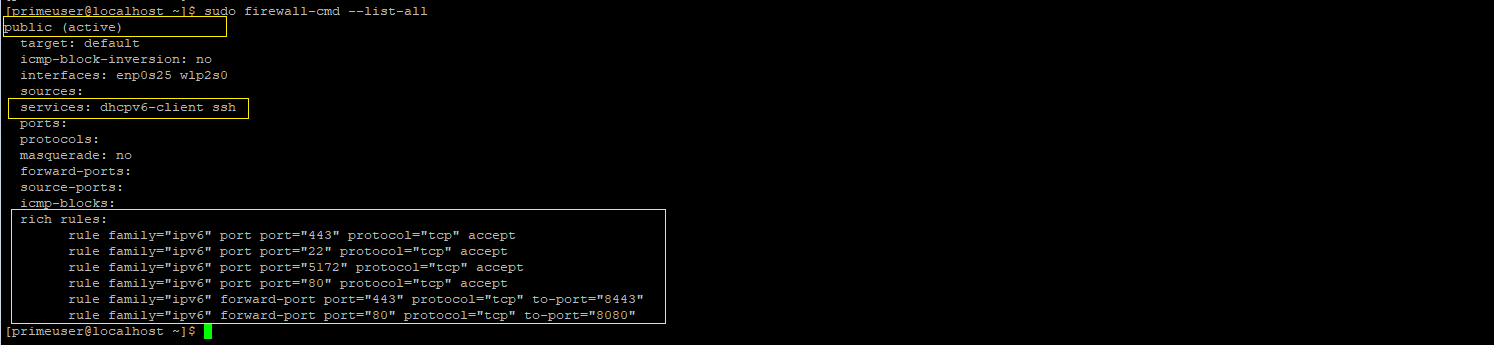
-
To configure firewalld for new OVA installation of Management Console allowing communication in an IPv6 environment perform the following steps:¶
PCoIP Management Console OVA comes ready for an IPv4 deployment. When deploying into an IPv6 environment, the firewalld IPv4 rules must be replaced with IPv6 rules. Perform the following steps to ensure Management Console only has IPv6 rules enabled after deploying Management Console OVA in an IPv6 environment.
-
Login to the Management Console host operating system console.
-
Close IPv4 22, 443, 80, 5172 ports.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --remove-port={22,443,80,5172}/tcp -
Remove IPv4 internal port forwarding from 443 to 8443.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --remove-forward-port=port=443:proto=tcp:toport=8443 -
Remove IPv4 internal port forwarding from 80 to 8080.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --remove-forward-port=port=80:proto=tcp:toport=8080 -
Open IPv6 port 443.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=443 protocol=tcp accept' -
Open IPv6 port 22.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=22 protocol=tcp accept' -
Open IPv6 port 5172.
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=5172 protocol=tcp accept' -
Open IPv6 port 80
sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 port port=80 protocol=tcp accept' -
Redirect IPv6 port 443 to 8443.
` sudo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-r
-
Redirect IPv6 port 80 to 8080.
udo firewall-cmd --zone=$(echo $def_zone) --permanent --add-rich-rule='rule family=ipv6 forward-port to-port=8080 protocol=tcp port=80' -
Reload the firewall rules.
Reload firewall rules -
Confirm the rules are applied.
-
Check the firewalld status is active.
sudo systemctl status firewalld

-
Verify all rules are added in firewalld or not, all rules should be applied.
sudo firewall-cmd --list-all
-