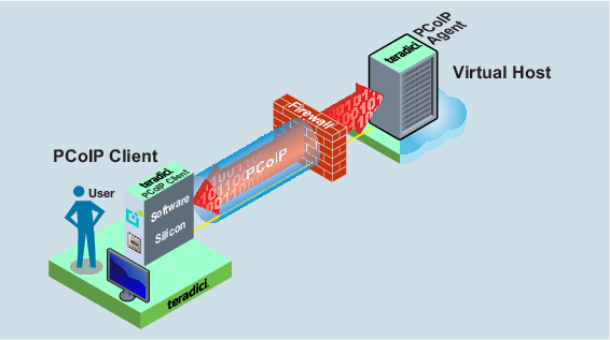
Deployment Scenarios¶
This section provides a few example deployments in which the Broker Protocol is used to establish a PCoIP session to remotely access a desktop or application.
External or WAN Deployments¶
The following diagram shows an example of a user using the Broker Protocol to establish a PCoIP session in a typical external or WAN deployment.
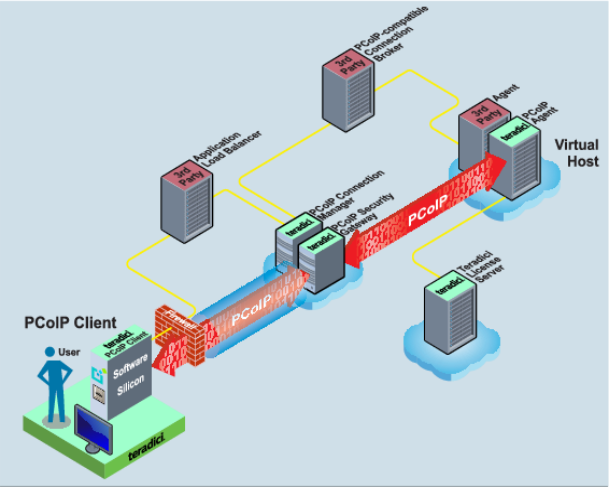
As seen in the diagram, the PCoIP Connection Manager enables the client and the agent to establish a remote desktop connection by creating a PCoIP session. The PCoIP Security Gateway enables WAN users to securely access their remote desktops via the Internet without setting up a VPN connection, while the connection broker authenticates the user and queries the desktop and applications.
In larger WAN deployments, multiple connection managers and security gateways should be deployed to provide high availability. A load balancer may then be deployed to distribute PCoIP sessions over the pairs of connection managers and security gateways. The load balancer should be an HTTPS reverse-proxy that supports cookie-based session stickiness.
The third-party broker agent component in the host desktop is an optional component used by the connection broker to manage and monitor the desktop state. The broker agent and PCoIP agent do not directly interact, but the broker agent may sample information about PCoIP sessions. As an example, the broker agent may query PCoIP session status through the PCoIP Windows WMI statistics counter on Windows hosts.
Internal LAN or VPN Deployments¶
The following diagram shows an example of a user using the Broker Protocol to establish a PCoIP session where clients are connected to the datacenter through a LAN or VPN.
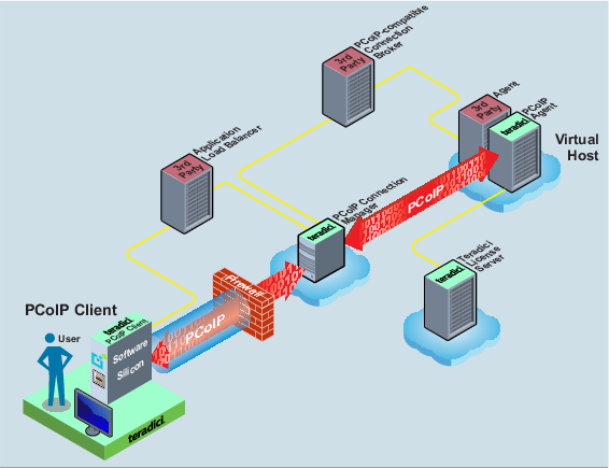
In this scenario, clients can directly communicate with the PCoIP agents, which eliminates the need for the PCoIP Security Gateway. In this case, the PCoIP Connection Manager would be deployed without a paired PCoIP Security Gateway, as shown in the diagram. The figure also shows an optional load balancer between the PCoIP client and the PCoIP Connection Managers.
When a deployment involves both internal and external deployments
In a typical deployment scenario involving both internal and external deployments, internal and external users may access the same data center by providing both a pool of external-facing connection managers paired with security gateways, and a pool of internal-facing connection managers without security gateways.
Multi-Factor Authentication Deployments¶
The broker is generally responsible for ensuring the connecting user has authorization to use the system and determining which resources the user should be presented with. With that principle, in a multi-factor authentication deployment, the broker is often responsible for performing the authentication, as shown in the following diagram.
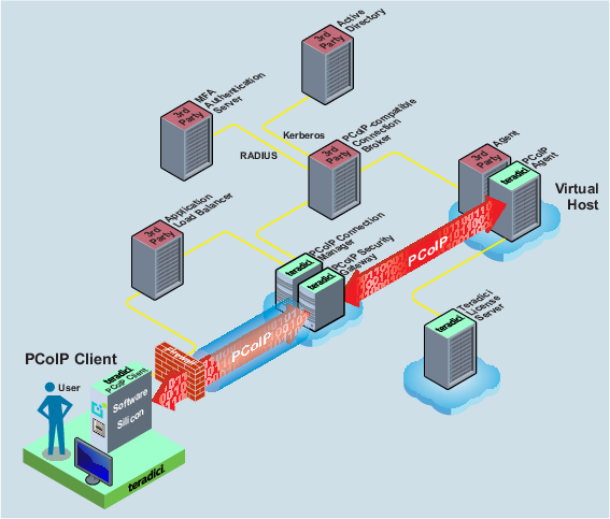
This diagram shows an example broker which uses Kerberos and RADIUS communications to back-end authentication servers. The Broker Protocol and the Teradici Cloud Access Software do not prescribe any particular structure on the broker or how it authenticates users.
Alternately, gateway or authentication appliances may perform one phase of the user authentication before allowing access to the broker. These appliances, not shown, may be placed inline in the Broker Protocol flow with a function similar to that of the PCoIP Connection Manager.
Direct-Connect Deployments¶
The Broker Protocol may also be used to establish a PCoIP session directly without using a connection broker. In the direct-connect deployment, the client uses the Broker Protocol to directly communicate with the remote resource to establish a PCoIP session. Direct-connect deployments are typically used in LAN-only scenarios. The following diagram illustrates a direct-connect deployment.